Background #
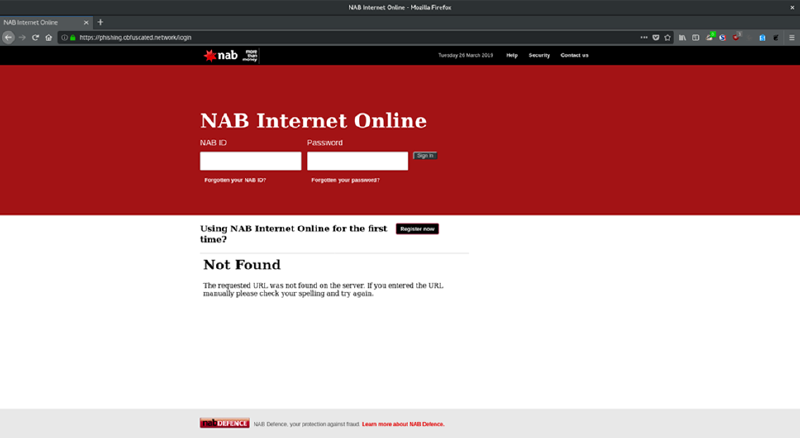
I know it may be hard to believe, but this poor looking website above is not the legitimate NAB website, it’s a poor mockery of a NABs internet banking portal based off a phishing kit we’ve seen. How do I know this? Because I made it.
It stemmed from a weird need, we often need to showcase our phishing capability to seniors in the bank and as a good educational piece to students and employees. Depending on who we’re showcasing to we’re either demonstrating how we respond and manage the risk to customers, or educating users for simple things they can identify to determine the legitimacy. It also helps to showcase the other side of the phishers themselves; a lot of people don’t seem to realise what’s being gathered.
The site itself is incredibly simple, it’s a python flask application I developed in a day, that uses the skin from a phishing kit we uncovered around that time. It had a couple of common tricks that we see with phishing kits, including redirecting to the legitimate NAB website after credentials were submitted, or if you went to the wrong URL. I had included the capability for IP and User Agent filtering, but I didn’t take advantage of those features.
Upon submitting to the site it’ll email the credentials along with the user agent and IP address that it originated from, to a Gmail account.
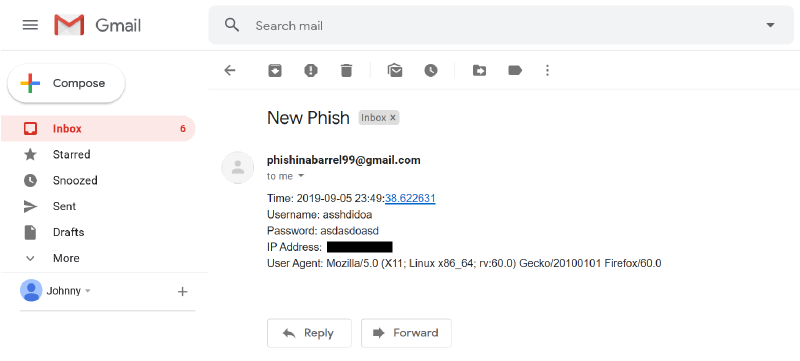
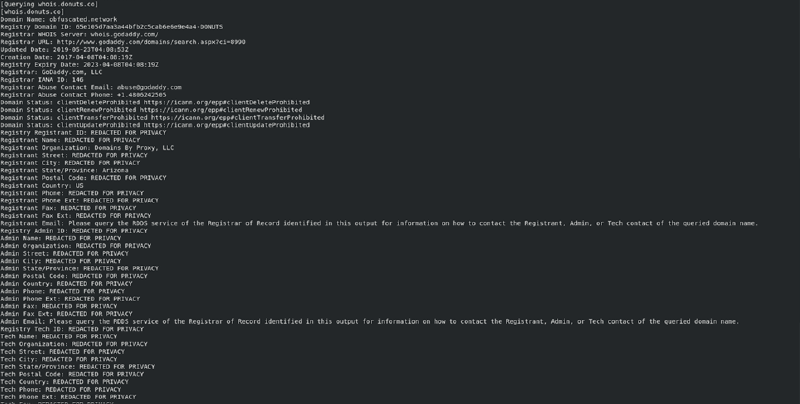
The site itself was using a domain name I owned and purchased through GoDaddy, (*.obfuscated.network), and was being hosted on a Singaporean VPS on DigitalOcean infrastructure.
Ther website became the keystone demonstration for student security workshops that we hosted and ran.
While I didn’t go into detail in regards to the remediation during that session, for other sessions with our senior executives we would.We had recently developed a series of automation playbooks using Splunk Phantom that has drastically improved our response process by automatically escalating to some third parties, and generating information used in tracking the impact including case notes, response and containment times and more.
Situation #
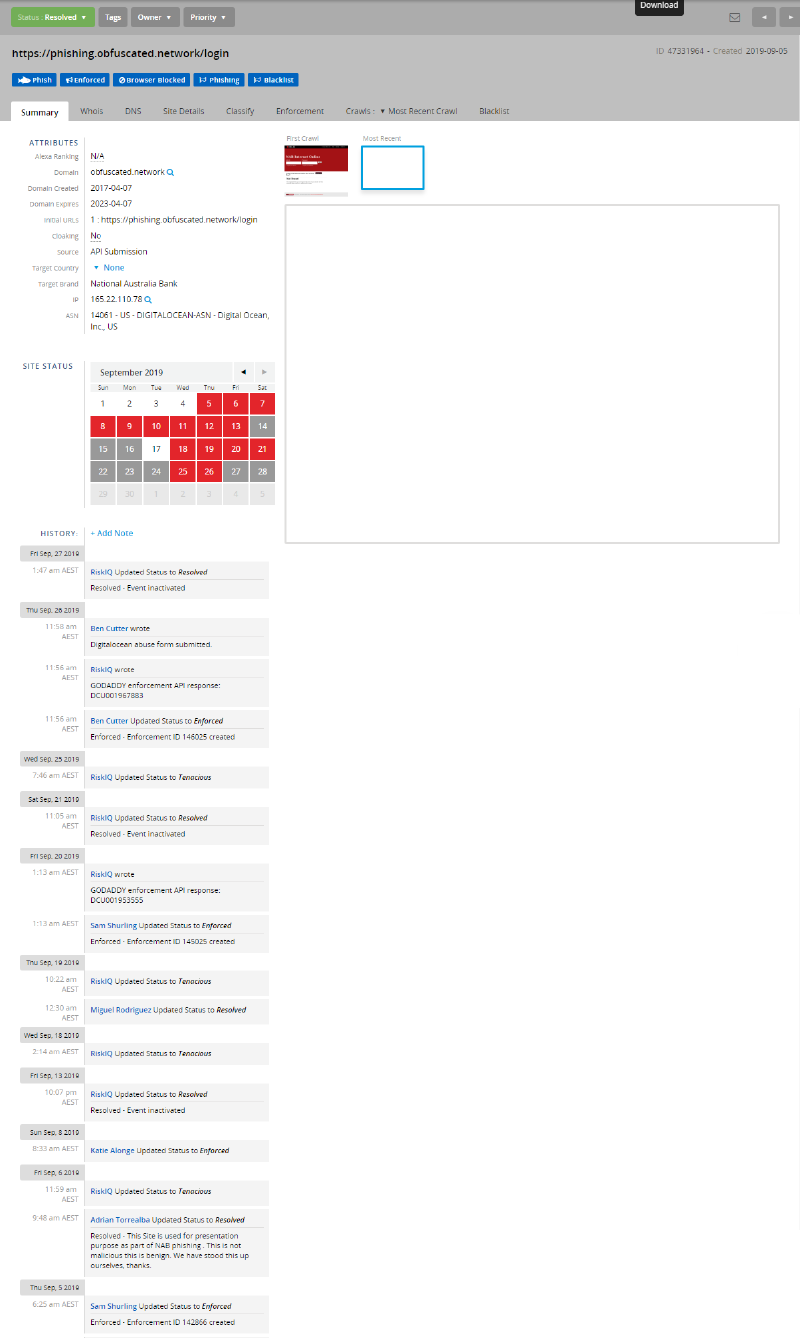
On the 4th of September 2019 as a part of a presentation to a senior executive we had added the domain to Phantom, it was given a ‘testing’ flag to reflect that it wasn’t malicious and not to action it, but an enthusiastic new member to the team didn’t see the flag and actioned it.
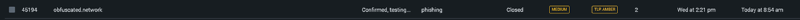
These are the lessons from that action, while it may seem like a negative at first, what we’ve gathered and determined from it in terms of the process some of our third parties provide has definitely been valuable.
We have two main third parties that we deal with: RiskIQ and F5 WebSafe. We previously used to submit to Phishtank, Google Safety Browse and more but currently the initial step for our Phantom playbook is to submit the domain to RiskIQ for them to action our takedowns.
On the 5th of September, at approximately 6am AEST that’s exactly what they did. RiskIQ did a simple whois lookup and saw that the privacy information of the owner of the domain (i.e: me) was all redacted. They identified the infrastructure it was hosted on (DigitalOcean), and manually submitted a takedown to the DigitalOcean abuse webform. At the same time they must have submitted the domain to Google Safe Browsing
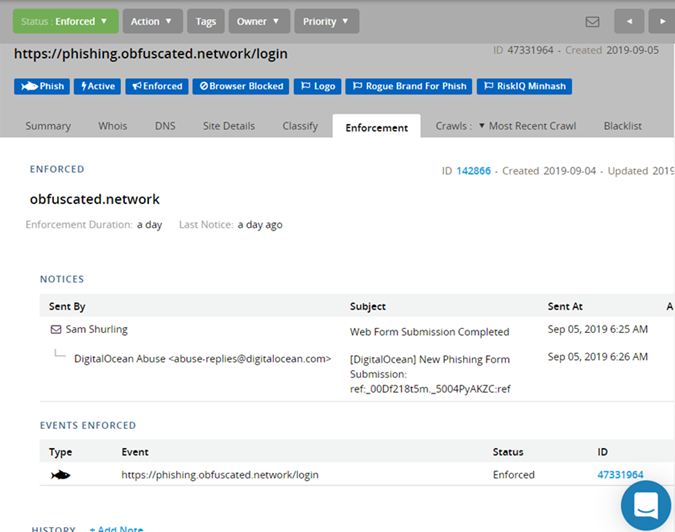
At approximately 5pm AEST the same day I received my first indicator that the domain had been flagged, and that was by pure luck. I had visited another subdomain that was also hosted on DigitalOcean and received the Google Safety Browse message, once I saw that I suspected something was up, and after validating had confirmed that the process was underway. My third domain that’s hosted on Google Cloud Platform was not impacted.
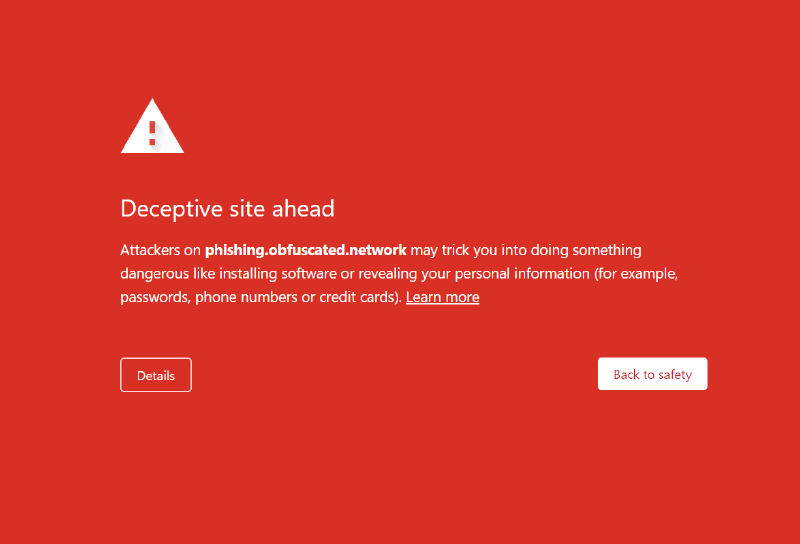
When Google Safe Browsing comes up, you can report the domain as a false positive, it brings up a simple dialog box where you can provide reasoning that it’s a false positive. I submitted that the same night and by the next morning (6th September) discovered that the Google Safe Browsing warning has been removed.
At the same time we informed RiskIQ via their portal that the site was used for presentation purposes and resolved the case.
On the 10th of September at approximately 3PM AEST F5 WebSafe had detected the domain and reported it to us. Again Google Safe Browsing had been resubmitted for the domain (and I had again issued a false positive report for it). On the end of the potential culprit I had not received any correspondence relating to my domain at this stage.
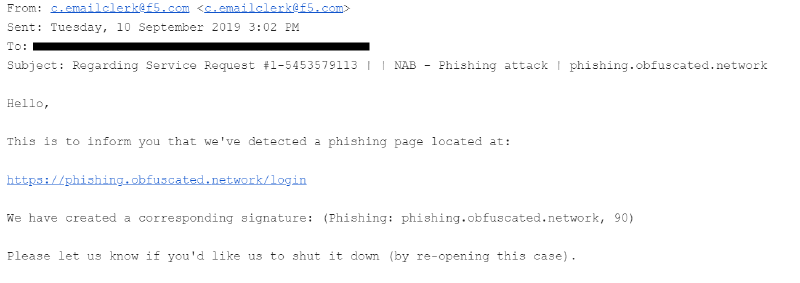
On the 13th of September I finally received a notification from DigitalOcean that my VPS instance had been compromised and was hosting a phishing site. Their request wanted to know what course of action I was taking to remediate it, what steps I would take to prevent it from recurring again in the future and in the meantime they had firewalled the host (although it was still publicly accessible to me - but potentially it was just cached).
In the ticket from DigitalOcean I could see the takedown notice from RiskIQ. I had responded back informing them that I was a NAB employee and that if they wished to validate they could contact NAB via email to confirm (nabcert.csoc@nab.com.au). Keep in mind that the DigitalOcean account has no connection to NAB, it’s signed up on a personal email address on a different domain that I own.
On the 17th of September 2019 I received a brief email from DigitalOcean informing me that they had removed the network block, and the issue was resolved - there had been no validation, simply saying that I worked for NAB and providing a publicly known email address that appeared legitimate was enough to have it removed.
On the 20th of September after a submission from RiskIQ to GoDaddy I received a notification from GoDaddy to my personal address. It was a simple notice telling me that there was a risk of my domain being suspended due to a violation of the terms and service. I ignored the email, waiting to see if they would suspend the domain or not.
On the 21st of September I received another email from GoDaddy, the domain had now been suspended which took the entire *.obfuscated.network domain off the internet (although the hosts were still present and accessible via IP address). Again I used the same tactic as last time, informing them that I’m a NAB staff member and it was a part of testing and validation (almost the exact same message as I had sent to DigitalOcean), if they wanted to validate they were free to contact nabcert.csoc@nab.com.au.
On the 24th of September I received a response from GoDaddy informing me that to validate that was true I’d have to send an email from the nab.com.au domain. I did this using the nabcert.csoc@nab.com.au email address and in minutes received a response informing me the issue was closed and my domain had been restored.
Lessons #
Since then I still have been battling with Google Safety Browse - which is now in place for the entire *.obfuscated.network domain even after multiple submissions, and the site has been resolved in RiskIQ. Otherwise the domain and site have been restored to full functionality.
Nevertheless it is filled with valuable lessons, whether targeted internal or external phishing I don’t think we fully comprehend the ease for a phisher to set up or continue a phishing campaign. As defenders we get lost constantly battling the waves, that we think we’re being quite the hindrance, especially after all of the dollars invested in products and services for easier detection and alerting.
On top of that there there’s obviously concerns about impacting legitimate customers, so validation takes time and slows the process down, and with no standardised medium for issuing takedowns it means that for different providers different approaches have to be issued.
Keep in mind that during this case I used some well known providers, if I had used something less reputable, I doubt there’d be the same response. I haven’t even mentioned Azure and the hellfire landscape of phishing that platform has become.
Phishing has always been presumed to be low hanging fruit purely in terms of customer gullibility and the potential reward, but through this example we can see that the challenge facing blue teams is even more difficult than originally anticipated.
Timeline #
4th September:
- Flagged in Phantom
- Added to RiskIQ
- Submitted to Google Safety Browse
5th September:
- RiskIQ escalated to DigitalOcean
6th September:
- We identified the domain had been added to Google Safety Browse
- Submitted response to Google Safety Browse and it was instantly updated to remove the warning.
- We flagged that it was testing in RiskIQ and for no further action to be completed, resolving the issue
10th September:
- F5 Websafe detect the domain and submit to us
- Google Safety Browse re-established
- Submitted response to Google Safety Browse (this time it’s for the entire *.obfuscated.network domain, and is still in place).
13th September:
- DigitalOcean receive RiskIQ ticket
- DigitalOcean contact account owner, firewalling VPS.
15th September:
- Responded to DigitalOcean ticket from private email account, informing them it’s a part of testing for NAB.
17th September:
- DigitalOcean respond and are satisfied with my response (no validation has taken place), and have removed the firewall.
20th September:
- RiskIQ have identified the domain as tenacious and issued an automated abuse case to GoDaddy
- Received warning of domain suspension from GoDaddy
21st September:
- GoDaddy suspended my domain - hosts are still active, but domain is no longer accessible.
- Responded to GoDaddy ticket from my personal address informing them that I’m a NAB employee and it was a part of testing (exactly like with DigitalOcean).
24th September:
- GoDaddy responded to my request, requiring validation from a user on the domain
- I sent them an email from nabcert.csoc@nab.com.au
- Minutes later they restored the domain status
- Another request was submitted to Google Safety Browse to inform them that the domain is not phishing, but it still remains in place.
27th September:
- Marked as resolve again in RiskIQ
- Google Safety Browse still in place.